

On Tuesday US government issued a warning about a new type of ransomware known as Bad Rabbit (Ransom: Win32/Tibbar.A). The Ransomware has mainly spread in Russia and Ukraine.
We are creating this guide to help you prevent/stop malicious Bad Rabbit ransomware from encrypting your computer.
Ransom: Win32/Tibbar.A dubbed Bad Rabbit is a ransomware like NotPetya and Wannacry. It doesn’t use exploits. It uses a drive-by attack: Victims download a false Adobe Flash installer from infected websites and physically launch the .exe file, hence infecting themselves.
In Some Cases, this ransomware attempts to reboot your PC so it can encrypt your files.
This ransomware stops victims from using their PC or accessing their data. It might ask infected computer owners to pay money to a malicious hacker.
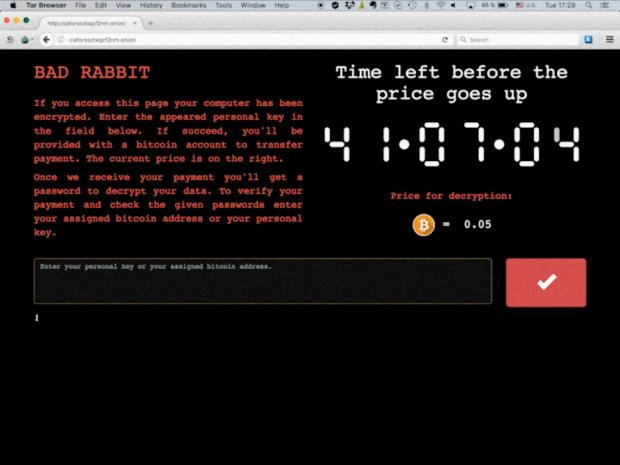
The criminals behind the Bad Rabbit attack are demanding 0.05 bitcoin as ransom — that’s approx. Rs. 19000 at the current exchange rate.
According to our data, most of the victims of these attacks are located in
This ransomware has infected devices through a number of hacked Russian media websites.
According to Microsoft the indicators of compromise are:

Bad Rabbit overwrites starts encrypting user content and then overwrites the Master Boot Record (MBR).
Extensions which are prone to this malware are:
.3ds, .7z, .accdb, .ai, .asm, .asp, .aspx, .avhd, .back, .bak, .bmp, .brw, .c, .cab, .cc, .cer, .cfg, .conf, .cpp, .crt, .cs, .ctl, .cxx, .dbf, .der, .dib, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .hpp, .hxx, .iso, .java, .jfif, .jpe, .jpeg, .jpg, .js, .kdbx, .key, .mail, .mdb, .msg, .nrg, .odc, .odf, .odg, .odi, .odm, .odp, .ods, .odt, .ora, .ost, .ova, .ovf, .p12, .p7b, .p7c, .pdf, .pem, .pfx, .php, .pmf, .png, .ppt, .pptx, .ps1, .pst, .pvi, .py, .pyc, .pyw, .qcow, .qcow2, .rar, .rb, .rtf, .scm, .sln, .sql, .tar, .tib, .tif, .tiff, .vb, .vbox, .vbs, .vcb, .vdi, .vfd, .vhd, .vhdx, .vmc, .vmdk, .vmsd, .vmtm, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xml, .xvd, .zip
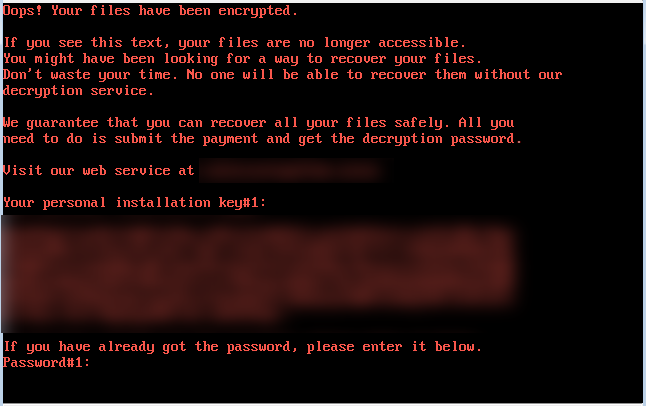
After a forced reboot, Victims are locked out of their computer and forced into pay ransom for a key to regain access. This message appears on infected computer and Victim can’t log in to operating system:

The message says:
“ Oops ! Your files have been encrypted.
If you see this text, your files are no longer accessible.
You might have been looking for a way to recover your files.
Don’t waste your time. No one will be able to recover them without our
decryption service.
We guarantee that you can recover all your files safely. All you
need to do is submit the payment and get the decryption password.
Visit our web service at <TOR .onion address>
Your personal installation key#<number>:
<key>
If you have already got the password, please enter it below.
Password#<number”
Visiting the mentioned .onion address provides a screen like shown below:

Maybe, the ransomware may try to connect to the network, so it can target and infect other computers.
It uses a hardcoded set of usernames and passwords to try to brute force into the network:
| · Admin | · Guest | · rdpuser |
| · Administrator | · manager | · root |
| · alex | · nas | · superuser |
| · asus | · nasadmin | · support |
| · backup | · nasuser | · Test |
| · boss | · netguest | · User |
| · buh | · operator | · User1 |
| · ftp | · other user | · user-1 |
| · ftpadmin | · rdp | · work |
| · ftpuser | · rdpadmin | |
| · 111111 | · Administrator | · qwer |
| · 123 | · administrator | · qwert |
| · 123321 | · Administrator123 | · qwerty |
| · 1234 | · administrator123 | · qwerty123 |
| · 12345 | · adminTest | · root |
| · 123456 | · god | · secret |
| · 1234567 | · Guest | · sex |
| · 12345678 | · guest | · test |
| · 123456789 | · Guest123 | · test123 |
| · 1234567890 | · guest123 | · uiop |
| · 321 | · love | · User |
| · 55555 | · password | · user |
| · 777 | · qwe | · User123 |
| · 77777 | · qwe123 | · user123 |
| · Admin | · qwe321 | · zxc |
| · Admin123 | · zxc123 | |
| · admin123Test123 | · zxc321 | |
| · zxcv |
Tips for everyone:
Source
https://www.kaspersky.com/blog/bad-rabbit-ransomware/19887/
https://www.microsoft.com/en-us/wdsi/threats/ransomware
http://money.cnn.com/2017/10/24/technology/bad-rabbit-ransomware-attack/index.html