

Last Friday the cyber world was hit by one of the most devastating cyber attack in the recent history. It is called “WannaCry” Ransomware. It has infected nearly 300,000 computers in 150 countries and is still at large.
It is considered very dangerous because of the thing that it done to your computer. Just think what would it like if you lost all of your computer data, for example things like family pictures, confidential documents or any important research data from your work. The only way to acquire that data is pay an anonymous person. You have to pay your money to get you own data. This is the new way of extortion which is done online and don’t left any traces while doing so.
In this guide we will try to answer most of the question related to what Ransomware is?, Where does it come from?, How you can prevent it from infecting your computer? And etc. So let’s start;
Ransomware is malicious software which executes the cryptoviral extortion attack. What it mean is that the Ransomware blocks any access (accept the attacker) to your data until you pay some kind of ransom to attacker. It also display a message requesting a fee to give it back to you.
Many of the basic type of Ransomware could be easily reversible by a knowledgeable hacker. But if it’s highly encrypted, that it will make most of the computer files inaccessible to you. It will encrypt your computers Master Class File (MFT) or if you are unlucky enough it will block the entire hard disk.
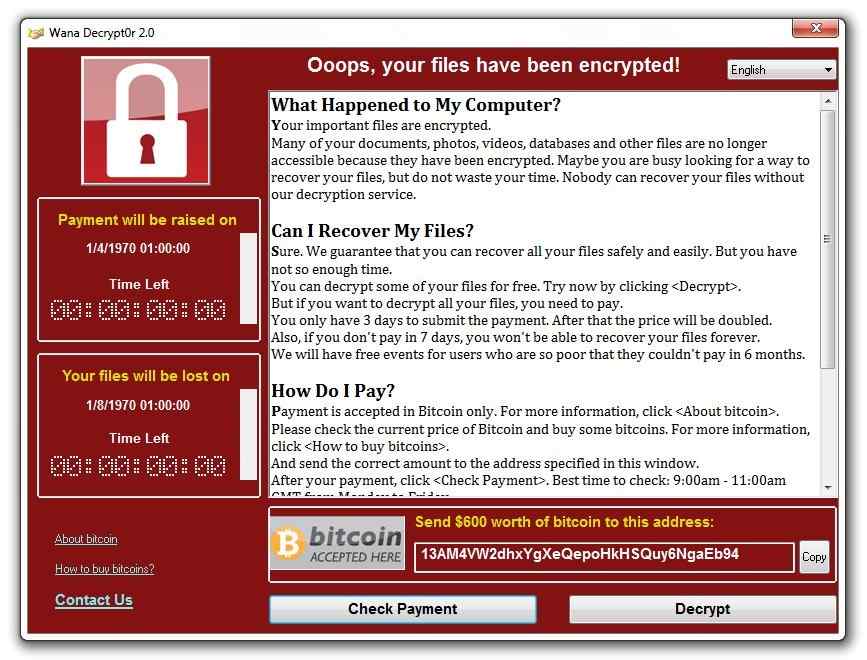
The WannaCry is a highly modified Ransomeware which is rapidly spreading across all over the cyberspace infecting “Windows” computer. It started spreading on Friday the 12 th May 2017. It affects the computer by exploiting a Windows component known as Server Message Block (SMB). You can look for the exploit with the name “ETERNALBLUE” on your Windows computer. As most of the Ransomware it will lock (encrypt) your hard disk. And, if you have other computers connected through LAN, It will laterally spread between them. Scary right!
This is how Wannacry Ransomware infected Britain’s health system and global shipper FedEx. Even the pirates are not safe, it is also stated that Disney movie “The Pirate of The Caribbean 5” has also been stolen by this Ransomware and the attackers are asking for a hefty price or they will made the movie public. It is believed that the creator of this malicious software is no other that the USA security agency known as the National Security Agency (NSA).
For most of the people, attackers are asking for hefty payments of $300 to $600 to restore access. Mode of payment is in Bitcoin. It is a digital currency which cannot be traced online.
Well the best way to prevent WannCrypt from infecting your computer is to be vigilant and “DO NOT” open any suspicious (even a little) email attachment.
As per Cyber Swachhta Kendra there are many file extensions that the Ransomware can latch on to. The file extensions are given below.
| Type Of Files | Extensions |
| Commonly used office file extensions | .ppt, .doc, .docx, .xlsx, .sxi |
| Less common and nation-specific office formats | .sxw, .odt, .hwp |
| Archives, media files | .zip, .rar, .tar, .bz2, .mp4, .mkv |
| Emails and email databases | .eml, .msg, .ost, .pst, .edb |
| Database files | .sql, .accdb, .mdb, .dbf, .odb, .myd |
| Developers’ source code and project files | .php, .java, .cpp, .pas, .asm |
| Graphic designers, artists and photographers files | .vsd, .odg, .raw, .nef, .svg, .psd |
| Encryption keys and certificates | .key, .pfx, .pem, .p12, .csr, .gpg, .aes |
| Virtual machine files | .vmx, .vmdk, .vdi |
“ How can I protect my computer running on windows XP or Windows Server 2003 from WannaCry?”
If you are still using windows older versions like Windows XP, Windows Server 2003 or Windows 8. You don’t have to fear anything because Microsoft has created the security updates for them too. ( Download links)
Q. Can I also run this update on my pirated Windows?
A. Maybe but we recommend you to use genuine version Windows to install updates.
Q. I am running Windows 10. Is it also vulnerable to Wannacry Ransomware attack?
A. No, the Ransomware is designed to infect outdated Windows i.e. Windows XP, Server 2003, 2003 R2, 2008 and Windows 7. So Windows 10 users are… For now.
Q. Is this update compatible with my Windows 2003 R2?
A. The Windows 2003 R2 updates are same as Windows 2003. So you will not have any issues.
Q. What if I don’t give admin rights to my clients? Am I safe then?
A. No. Once WannaCrypt Ransomware executes itself, there is no turning back. It will encrypt all the files it can reach in your computer or any other computer connected to yours via LAN. It will also try making some registry changes in HKLM hive which require Admin authority and also tries to disable shadow copies on your pc. Hence the computer will be infected whether the user has admin rights or not.
Q. Am I safe from any future malware or Ransomware attacks?
A. No. Applying the recent Microsoft update will only stop the Ransomware from spreading. The security update cannot protect against the infection itself.